I like to ask the community if there’s any specific Private only Router setup (not gateway) but service as host-proxy endpoint
I configured a router without listener (it just dial to public router ) and connected. no issues.
Services hosted via this router get connected from public router to this private router.
1.However I saw ziti edge client logs , it did attempt to connect to this private router but failed of course since it is not listening for connections.
2. Edge client logs shown it connected to 1 of the public router i set (#all) and from public router it managed to connect to the service as intended.
Is there a router.yaml that will not let edge client to attempt to it?
- router policy in zac ?
- router.yaml?
- or as per screenshot , turn off Traversal ?
You could certainly do it by changing your edge-router policies. You "probably" have an #all/#all policy? If that's the case, I would change that and use a #public/#all type of policy instead.
For any router you WANT edge devices to connect to, add an attribute to those routers called "public" (or 'edge' or 'access' or 'whatever' you want to call it).
Then ensure your edge router policy states that any router with the #public attribute can be used by #all clients and then you'll have the setup you want. (Assuming I understand what you're looking for)
This is how I generally setup my own overlays. the "actually public" routers get a "public" attribute, then i assign all identities access to the 'public' routers...
hth
Yes , on my smaller setup I doing it manually and works.
One this global scale setup I set policy to #all so all edge can connect to any global public edge we deployed (I am doing my own orchestration)
For now it is working just annoyed to see edge client trying to connect to these private router although they can't since I disabled listener.
To orchestrate different group of edge to use specific region public routers perhaps I need to manipulate in the orchestrator. I was hoping for an easier way out haha
Thanks I will explore on these to see how to add some regional attributes automatically via orchestrator
@TheLumberjack I think i would do the following but like to hear your views before committing
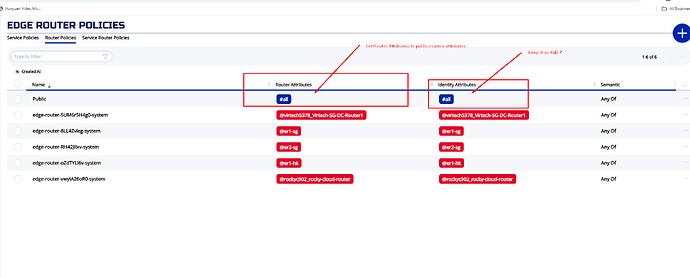
I would set Router Attributes to SG, HK ,JPN etc. (tied to our public routers attributes group)
keeping identity as all since we want all identities to have access to these public edge routers and using it to connect to their private edge.
the concern is on private edge below (in Red) i assumed they would be able to connect to public router since identity set to all right ?
Edge Client (#all) –> Public Routers (SG,HK,JPN etc.) –> Private Router –>Service
Hope i am thinking it correctly.
Sounds like you understand what i was trying to convey.
I'm not sure where/what the concern is. These other policies are system generated and are specific to each router. Those apply only to the router.
The public routers would be the onboarding routers for identities into the OpenZiti fabric. Once connected, those identities would be able to leverage any private routers for offloading traffic assuming those private routers are authorized for the identity and service being dialed. (Hopefully that makes sense)
First, add the attributes to your routers (you didn't show those, i assume you did that). Once the attributes are added, you would change that one #all to #SG, #JPN, etc. I think you understand
Thanks for your replies. Not really a technical concern but trying to figure out more.
i think #all #all in router policies is the reason why edge client tried to connect to it but got refused
if my public router set according to #SG #JP # HK etc. and identity #all this should fixed .
Was just trying to seek clarification from the community since i am planning for production roll out.
in short:
Router policies as shown - Changed #all to more specific group(attribute) while identity remain all since we want any edge client to utilize these global public router as transit.
Is my understanding correct?
Yes. Your understanding is correct.
thanks @TheLumberjack
I confirmed after setting this, no more errors of edge attempting trying to connect a private edge.
This allowed me to exposed only managed Public edge to tenants.
1 Like