Hi again, I am working towards how to control all outbound traffic to a public SaaS service like Google Workspace? I would like to be able to control access to certain public services from known IP addresses.
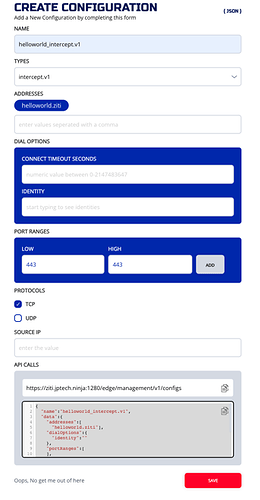
I am trying to duplicate the features of the sample quick start example on Netfoundry, shown in the screenshots below. Can you correct me if I understand this or not?
- The
sample.tools.netfoundry.iois a Service, it’s destination address can only be accessed via the Fabric. - A computer with the agent installed and enrolled is an Endpoint.
- The INTERCEPT HOST NAME / IP is MY service hostname on the fabric like
my.super.private - The HOST CONFIGURATION is the destination, like
google.com, including the protocol and port. - The outbound traffic is through the selected Edge Router.
- The App/WAN is what associates the Service with an Endpoints. The attributes fields accept individual objects or tags/groups of these objects. If I put the tag of
#all, then this service will work for any Endpoint or Service. - To create more such Services I need to make an associated App/WAN to connect the Service to Endpoint(s).
As a result of this arrangement. All traffic between my endpoints and the host my.super.private will exit fabric from the IP address of the Edge Router. Is this right?
Also, how does the Endpoint resolve my Service hostname in this case?
Edit: I was able to the get ZAC working in docker, and I see the console is quite different than the NetFoundry one. So there are some taxonomy differences, perhaps?