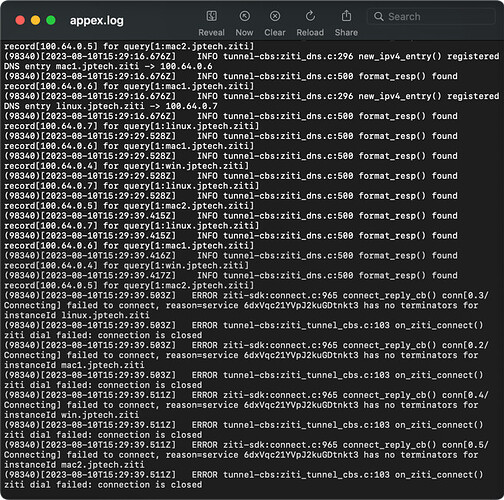
Update, I have this log in the edgerouter. [service 77OCwbctFezGe4tYTQ5ZgD has no terminators for instanceId win.jptech.ziti]
ziti-edge-router_1 | [16360.410] WARNING edge/router/xgress_edge.(*edgeClientConn).processConnect [ch{edge}->u{classic}->i{Vq7p}]: {type=[EdgeConnectType] chSeq=[92] edgeSeq=[0] error=[service 77OCwbctFezGe4tYTQ5ZgD has no terminators for instanceId win.jptech.ziti] token=[be8332ac-0f5c-4adb-8ee6-f94a47670bc2] connId=[72]} failed to dial fabric
When it is successful there is no output on the logs.
Here is the full output of the identities. It’s late, and I can’t tell the difference between the mac1... identitity that I CAN connect to and all the other ones.
{
"data": [
{
"_links": {
"auth-policies": {
"href": "./auth-policies/default"
},
"authenticators": {
"href": "./identities/1DDBNiwGV/authenticators"
},
"edge-router-policies": {
"href": "./identities/1DDBNiwGV/edge-router-policies"
},
"edge-routers": {
"href": "./identities/1DDBNiwGV/edge-routers"
},
"enrollments": {
"href": "./identities/1DDBNiwGV/enrollments"
},
"failed-service-requests": {
"href": "./identities/1DDBNiwGV/failed-service-requests"
},
"posture-data": {
"href": "./identities/1DDBNiwGV/posture-data"
},
"self": {
"href": "./identities/1DDBNiwGV"
},
"service-configs": {
"href": "./identities/1DDBNiwGV/service-configs"
},
"service-policies": {
"href": "./identities/1DDBNiwGV/service-policies"
},
"services": {
"href": "./identities/1DDBNiwGV/services"
}
},
"createdAt": "2023-08-08T03:05:22.342Z",
"id": "1DDBNiwGV",
"tags": {},
"updatedAt": "2023-08-08T03:56:36.813Z",
"appData": {},
"authPolicy": {
"_links": {
"self": {
"href": "./auth-policies/default"
}
},
"entity": "auth-policies",
"id": "default",
"name": "Default"
},
"authPolicyId": "default",
"authenticators": {
"cert": {
"id": "OYxUjbw5V"
}
},
"defaultHostingCost": 0,
"defaultHostingPrecedence": "default",
"disabled": false,
"enrollment": {},
"envInfo": {
"arch": "x86_64",
"os": "Linux",
"osRelease": "6.1.0-9-cloud-amd64",
"osVersion": "#1 SMP PREEMPT_DYNAMIC Debian 6.1.27-1 (2023-05-08)"
},
"externalId": null,
"hasApiSession": true,
"hasEdgeRouterConnection": true,
"isAdmin": false,
"isDefaultAdmin": false,
"isMfaEnabled": false,
"name": "mac1.jptech.ziti",
"roleAttributes": [
"admin",
"jptech",
"ssh"
],
"sdkInfo": {
"appId": "ziti-edge-tunnel",
"appVersion": "v0.21.5-local",
"branch": "HEAD",
"revision": "d7f329f",
"type": "ziti-sdk-c",
"version": "0.32.8"
},
"serviceHostingCosts": {},
"serviceHostingPrecedences": {},
"type": {
"_links": {
"self": {
"href": "./identity-types/Device"
}
},
"entity": "identity-types",
"id": "Device",
"name": "Device"
},
"typeId": "Device"
},
{
"_links": {
"auth-policies": {
"href": "./auth-policies/default"
},
"authenticators": {
"href": "./identities/6bNWqyt0o/authenticators"
},
"edge-router-policies": {
"href": "./identities/6bNWqyt0o/edge-router-policies"
},
"edge-routers": {
"href": "./identities/6bNWqyt0o/edge-routers"
},
"enrollments": {
"href": "./identities/6bNWqyt0o/enrollments"
},
"failed-service-requests": {
"href": "./identities/6bNWqyt0o/failed-service-requests"
},
"posture-data": {
"href": "./identities/6bNWqyt0o/posture-data"
},
"self": {
"href": "./identities/6bNWqyt0o"
},
"service-configs": {
"href": "./identities/6bNWqyt0o/service-configs"
},
"service-policies": {
"href": "./identities/6bNWqyt0o/service-policies"
},
"services": {
"href": "./identities/6bNWqyt0o/services"
}
},
"createdAt": "2023-08-01T03:45:41.002Z",
"id": "6bNWqyt0o",
"tags": {},
"updatedAt": "2023-08-08T06:26:31.959Z",
"appData": {},
"authPolicy": {
"_links": {
"self": {
"href": "./auth-policies/default"
}
},
"entity": "auth-policies",
"id": "default",
"name": "Default"
},
"authPolicyId": "default",
"authenticators": {
"cert": {
"id": "htX4UJt0o"
}
},
"defaultHostingCost": 0,
"defaultHostingPrecedence": "default",
"disabled": false,
"enrollment": {},
"envInfo": {
"arch": "x86_64",
"os": "Linux",
"osRelease": "6.1.0-10-amd64",
"osVersion": "#1 SMP PREEMPT_DYNAMIC Debian 6.1.38-1 (2023-07-14)"
},
"externalId": null,
"hasApiSession": true,
"hasEdgeRouterConnection": true,
"isAdmin": false,
"isDefaultAdmin": false,
"isMfaEnabled": false,
"name": "macbian",
"roleAttributes": [
"admin",
"jptech",
"ssh"
],
"sdkInfo": {
"appId": "ziti-edge-tunnel",
"appVersion": "v0.21.5-local",
"branch": "HEAD",
"revision": "d7f329f",
"type": "ziti-sdk-c",
"version": "0.32.8"
},
"serviceHostingCosts": {},
"serviceHostingPrecedences": {},
"type": {
"_links": {
"self": {
"href": "./identity-types/Device"
}
},
"entity": "identity-types",
"id": "Device",
"name": "Device"
},
"typeId": "Device"
},
{
"_links": {
"auth-policies": {
"href": "./auth-policies/default"
},
"authenticators": {
"href": "./identities/7ARsJMakq/authenticators"
},
"edge-router-policies": {
"href": "./identities/7ARsJMakq/edge-router-policies"
},
"edge-routers": {
"href": "./identities/7ARsJMakq/edge-routers"
},
"enrollments": {
"href": "./identities/7ARsJMakq/enrollments"
},
"failed-service-requests": {
"href": "./identities/7ARsJMakq/failed-service-requests"
},
"posture-data": {
"href": "./identities/7ARsJMakq/posture-data"
},
"self": {
"href": "./identities/7ARsJMakq"
},
"service-configs": {
"href": "./identities/7ARsJMakq/service-configs"
},
"service-policies": {
"href": "./identities/7ARsJMakq/service-policies"
},
"services": {
"href": "./identities/7ARsJMakq/services"
}
},
"createdAt": "2023-07-30T06:37:55.403Z",
"id": "7ARsJMakq",
"tags": {},
"updatedAt": "2023-07-30T06:37:55.403Z",
"appData": {},
"authPolicy": {
"_links": {
"self": {
"href": "./auth-policies/default"
}
},
"entity": "auth-policies",
"id": "default",
"name": "Default"
},
"authPolicyId": "default",
"authenticators": {
"updb": {
"id": "7pR6JoukZ5",
"username": "admin"
}
},
"defaultHostingCost": 0,
"defaultHostingPrecedence": "default",
"disabled": false,
"enrollment": {},
"envInfo": {},
"externalId": null,
"hasApiSession": true,
"hasEdgeRouterConnection": false,
"isAdmin": true,
"isDefaultAdmin": true,
"isMfaEnabled": false,
"name": "Default Admin",
"roleAttributes": null,
"sdkInfo": {},
"serviceHostingCosts": {},
"serviceHostingPrecedences": {},
"type": {
"_links": {
"self": {
"href": "./identity-types/User"
}
},
"entity": "identity-types",
"id": "User",
"name": "User"
},
"typeId": "User"
},
{
"_links": {
"auth-policies": {
"href": "./auth-policies/default"
},
"authenticators": {
"href": "./identities/fM9mAb.Gs/authenticators"
},
"edge-router-policies": {
"href": "./identities/fM9mAb.Gs/edge-router-policies"
},
"edge-routers": {
"href": "./identities/fM9mAb.Gs/edge-routers"
},
"enrollments": {
"href": "./identities/fM9mAb.Gs/enrollments"
},
"failed-service-requests": {
"href": "./identities/fM9mAb.Gs/failed-service-requests"
},
"posture-data": {
"href": "./identities/fM9mAb.Gs/posture-data"
},
"self": {
"href": "./identities/fM9mAb.Gs"
},
"service-configs": {
"href": "./identities/fM9mAb.Gs/service-configs"
},
"service-policies": {
"href": "./identities/fM9mAb.Gs/service-policies"
},
"services": {
"href": "./identities/fM9mAb.Gs/services"
}
},
"createdAt": "2023-08-08T03:05:28.537Z",
"id": "fM9mAb.Gs",
"tags": {},
"updatedAt": "2023-08-08T06:12:11.511Z",
"appData": {},
"authPolicy": {
"_links": {
"self": {
"href": "./auth-policies/default"
}
},
"entity": "auth-policies",
"id": "default",
"name": "Default"
},
"authPolicyId": "default",
"authenticators": {
"cert": {
"id": "oY6Unb.5s"
}
},
"defaultHostingCost": 0,
"defaultHostingPrecedence": "default",
"disabled": false,
"enrollment": {},
"envInfo": {
"arch": "x86_64",
"os": "Linux",
"osRelease": "6.1.0-9-cloud-amd64",
"osVersion": "#1 SMP PREEMPT_DYNAMIC Debian 6.1.27-1 (2023-05-08)"
},
"externalId": null,
"hasApiSession": true,
"hasEdgeRouterConnection": false,
"isAdmin": false,
"isDefaultAdmin": false,
"isMfaEnabled": false,
"name": "mac2.jptech.ziti",
"roleAttributes": [
"jptech",
"ssh"
],
"sdkInfo": {
"appId": "ziti-edge-tunnel",
"appVersion": "v0.21.5-local",
"branch": "HEAD",
"revision": "d7f329f",
"type": "ziti-sdk-c",
"version": "0.32.8"
},
"serviceHostingCosts": {},
"serviceHostingPrecedences": {},
"type": {
"_links": {
"self": {
"href": "./identity-types/Device"
}
},
"entity": "identity-types",
"id": "Device",
"name": "Device"
},
"typeId": "Device"
},
{
"_links": {
"auth-policies": {
"href": "./auth-policies/default"
},
"authenticators": {
"href": "./identities/fmI.Nbw5Vl/authenticators"
},
"edge-router-policies": {
"href": "./identities/fmI.Nbw5Vl/edge-router-policies"
},
"edge-routers": {
"href": "./identities/fmI.Nbw5Vl/edge-routers"
},
"enrollments": {
"href": "./identities/fmI.Nbw5Vl/enrollments"
},
"failed-service-requests": {
"href": "./identities/fmI.Nbw5Vl/failed-service-requests"
},
"posture-data": {
"href": "./identities/fmI.Nbw5Vl/posture-data"
},
"self": {
"href": "./identities/fmI.Nbw5Vl"
},
"service-configs": {
"href": "./identities/fmI.Nbw5Vl/service-configs"
},
"service-policies": {
"href": "./identities/fmI.Nbw5Vl/service-policies"
},
"services": {
"href": "./identities/fmI.Nbw5Vl/services"
}
},
"createdAt": "2023-08-08T03:05:35.962Z",
"id": "fmI.Nbw5Vl",
"tags": {},
"updatedAt": "2023-08-08T06:09:29.573Z",
"appData": {},
"authPolicy": {
"_links": {
"self": {
"href": "./auth-policies/default"
}
},
"entity": "auth-policies",
"id": "default",
"name": "Default"
},
"authPolicyId": "default",
"authenticators": {
"cert": {
"id": "yx6UjiwGV"
}
},
"defaultHostingCost": 0,
"defaultHostingPrecedence": "default",
"disabled": false,
"enrollment": {},
"envInfo": {
"arch": "x86_64",
"os": "Linux",
"osRelease": "6.1.0-9-cloud-amd64",
"osVersion": "#1 SMP PREEMPT_DYNAMIC Debian 6.1.27-1 (2023-05-08)"
},
"externalId": null,
"hasApiSession": true,
"hasEdgeRouterConnection": false,
"isAdmin": false,
"isDefaultAdmin": false,
"isMfaEnabled": false,
"name": "win.jptech.ziti",
"roleAttributes": [
"jptech",
"ssh"
],
"sdkInfo": {
"appId": "ziti-edge-tunnel",
"appVersion": "v0.21.5-local",
"branch": "HEAD",
"revision": "d7f329f",
"type": "ziti-sdk-c",
"version": "0.32.8"
},
"serviceHostingCosts": {},
"serviceHostingPrecedences": {},
"type": {
"_links": {
"self": {
"href": "./identity-types/Device"
}
},
"entity": "identity-types",
"id": "Device",
"name": "Device"
},
"typeId": "Device"
},
{
"_links": {
"auth-policies": {
"href": "./auth-policies/default"
},
"authenticators": {
"href": "./identities/gveVhi.Gs/authenticators"
},
"edge-router-policies": {
"href": "./identities/gveVhi.Gs/edge-router-policies"
},
"edge-routers": {
"href": "./identities/gveVhi.Gs/edge-routers"
},
"enrollments": {
"href": "./identities/gveVhi.Gs/enrollments"
},
"failed-service-requests": {
"href": "./identities/gveVhi.Gs/failed-service-requests"
},
"posture-data": {
"href": "./identities/gveVhi.Gs/posture-data"
},
"self": {
"href": "./identities/gveVhi.Gs"
},
"service-configs": {
"href": "./identities/gveVhi.Gs/service-configs"
},
"service-policies": {
"href": "./identities/gveVhi.Gs/service-policies"
},
"services": {
"href": "./identities/gveVhi.Gs/services"
}
},
"createdAt": "2023-08-08T03:06:23.577Z",
"id": "gveVhi.Gs",
"tags": {},
"updatedAt": "2023-08-08T03:06:23.577Z",
"appData": {},
"authPolicy": {
"_links": {
"self": {
"href": "./auth-policies/default"
}
},
"entity": "auth-policies",
"id": "default",
"name": "Default"
},
"authPolicyId": "default",
"authenticators": {},
"defaultHostingCost": 0,
"defaultHostingPrecedence": "default",
"disabled": false,
"enrollment": {
"ott": {
"expiresAt": "2023-08-15T03:06:23.578Z",
"id": "gEeV4i.5Vl",
}
},
"envInfo": {},
"externalId": null,
"hasApiSession": false,
"hasEdgeRouterConnection": false,
"isAdmin": false,
"isDefaultAdmin": false,
"isMfaEnabled": false,
"name": "ios.jptech.ziti",
"roleAttributes": [
"admin",
"notech",
"ssh"
],
"sdkInfo": {},
"serviceHostingCosts": {},
"serviceHostingPrecedences": {},
"type": {
"_links": {
"self": {
"href": "./identity-types/Device"
}
},
"entity": "identity-types",
"id": "Device",
"name": "Device"
},
"typeId": "Device"
},
{
"_links": {
"auth-policies": {
"href": "./auth-policies/default"
},
"authenticators": {
"href": "./identities/pE4Bv1tDS/authenticators"
},
"edge-router-policies": {
"href": "./identities/pE4Bv1tDS/edge-router-policies"
},
"edge-routers": {
"href": "./identities/pE4Bv1tDS/edge-routers"
},
"enrollments": {
"href": "./identities/pE4Bv1tDS/enrollments"
},
"failed-service-requests": {
"href": "./identities/pE4Bv1tDS/failed-service-requests"
},
"posture-data": {
"href": "./identities/pE4Bv1tDS/posture-data"
},
"self": {
"href": "./identities/pE4Bv1tDS"
},
"service-configs": {
"href": "./identities/pE4Bv1tDS/service-configs"
},
"service-policies": {
"href": "./identities/pE4Bv1tDS/service-policies"
},
"services": {
"href": "./identities/pE4Bv1tDS/services"
}
},
"createdAt": "2023-07-30T06:38:01.645Z",
"id": "pE4Bv1tDS",
"tags": {},
"updatedAt": "2023-08-08T06:13:26.473Z",
"appData": {},
"authPolicy": {
"_links": {
"self": {
"href": "./auth-policies/default"
}
},
"entity": "auth-policies",
"id": "default",
"name": "Default"
},
"authPolicyId": "default",
"authenticators": {},
"defaultHostingCost": 0,
"defaultHostingPrecedence": "default",
"disabled": false,
"enrollment": {},
"envInfo": {
"arch": "amd64",
"os": "linux",
"osRelease": "6.1.0-10-amd64",
"osVersion": "#1 SMP PREEMPT_DYNAMIC Debian 6.1.38-1 (2023-07-14)"
},
"externalId": null,
"hasApiSession": true,
"hasEdgeRouterConnection": true,
"isAdmin": false,
"isDefaultAdmin": false,
"isMfaEnabled": false,
"name": "ziti-edge-router",
"roleAttributes": null,
"sdkInfo": {
"appId": "ziti-router",
"appVersion": "v0.29.0",
"branch": "main",
"revision": "3ca2dd2f4e7b",
"type": "ziti-router:tunnel",
"version": "v0.29.0"
},
"serviceHostingCosts": {},
"serviceHostingPrecedences": {},
"type": {
"_links": {
"self": {
"href": "./identity-types/Router"
}
},
"entity": "identity-types",
"id": "Router",
"name": "Router"
},
"typeId": "Router"
}
],
"meta": {
"filterableFields": [
"tags",
"roleAttributes",
"externalId",
"createdAt",
"updatedAt",
"isSystem",
"name",
"type",
"authPolicyId",
"isAdmin",
"isDefaultAdmin",
"id"
],
"pagination": {
"limit": 10,
"offset": 0,
"totalCount": 11
}
}
}