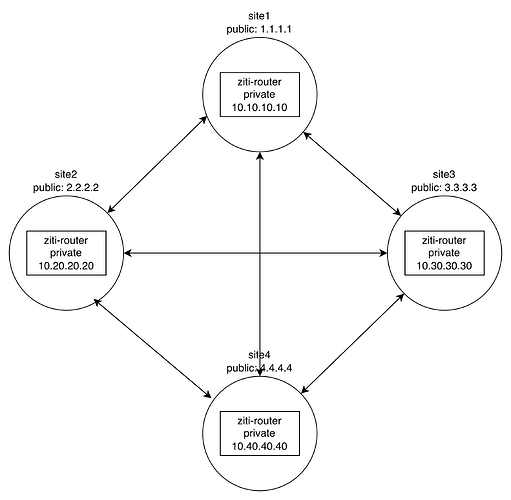
I want to have remote sites create a full mesh with each other, like below.
My question is how to configure the routers so that 1) internal things to the site can reach the router, and 2) each site can reach the router.
I understand how to use attributes to force identities and services to bind to specific routers. Assume that each site would have the right ports forwarded into their respective ziti-router instances.
Do I need to set up split DNS (like router.site1.domain.com) which resolves to the public IP address when resolved from other sites, but resolves to the internal IP when resolved from the local site? Or is there a better way to do it?
I know another option would be to have the firewall at each site reflect traffic back through port forwarding, but I would like to avoid burdening the firewall with that kind of traffic if the payloads are staying local to the site.
Thanks!
Hi @Krishopper ,
I'm not quite clear on what your goal is.
You've got routers, each with a private address and a public address. The routers need to talk to each other and identities need to talk to the routers.
Do you want:
- Routers to talk to each other on the public addresses?
- identities to talk to the routers on the private addresses?
Or is it more that you want both router and identities to talk to routers on private IPs if they're local but on public IPs if they're not?
If it's helpful, router links have a separate advertise address from the edge listener. So you can have:
link:
listeners:
- binding: transport
bind: tls:0.0.0.0:9001
advertise: tls:1.1.1.1:9001
listeners:
- binding: edge
address: tls:0.0.0.0:8001
options:
advertise: 10.10.10.10:8001
Thank you,
Paul
Do you want:
-
Routers to talk to each other on the public addresses?
-
Identities to talk to the routers on the private addresses?
Yes, this is excatly what I want.
If it's helpful, router links have a separate advertise address from the edge listener.
I missed this! Thank you for pointing that out.
Does the advertise: option have to match the name of the router for the TLS certificate?
Thanks for your patience with these questions while I’m learning about the security and authorization flows and such.
Yes. Otherwise, when connections are dialed to the router, they won't ever be trusted. All OpenZiti connections are mTLS so it's mandatory.
Note that you can supply multiple DNS names and IP addresses in the router config, which will be used to generate the router certificate:
csr:
country: US
province: NC
locality: Charlotte
organization: NetFoundry
organizationalUnit: Ziti
# (required) SANs that this router's certs should contain. At least one IP or DNS SAN should be defined that matches
# the edge listeners "advertise" value from the "listeners" section.
sans:
dns:
- "localhost"
- "test-network"
- "test-network.localhost"
- "ziti-dev-ingress01"
email:
- "admin@example.com"
ip:
- "127.0.0.1"
uri:
- "ziti://ziti-dev-router01/made/up/example"
So your router can match both internal and external IPs as well as whatever DNS names are appropriate.
Paul