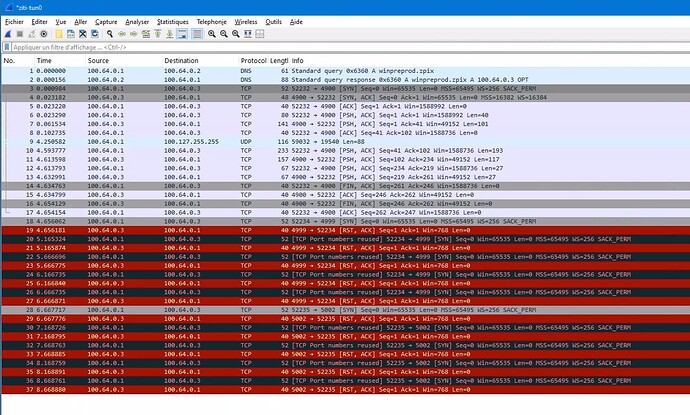
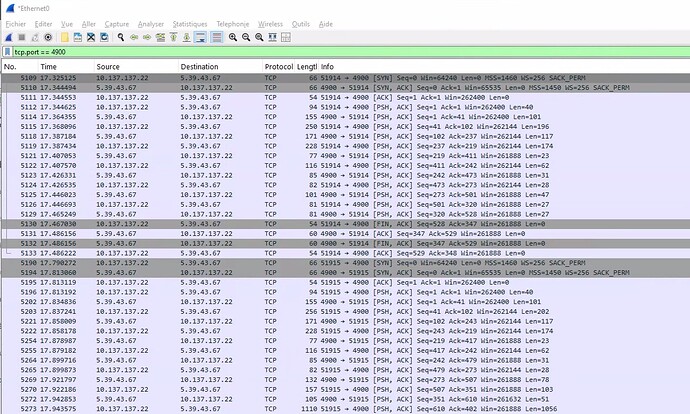
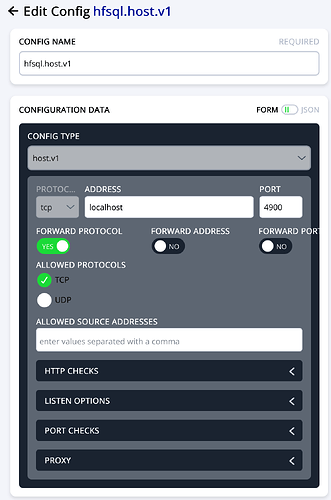
Hi Shawn,
1. IP address is fixed
2. services status
eric@zpix:~$ systemctl status ziti-controller.service
● ziti-controller.service - OpenZiti Controller
Loaded: loaded (/lib/systemd/system/ziti-controller.service; **enabled**; preset: **enabled**)
Drop-In: /etc/systemd/system/ziti-controller.service.d
└─override.conf
Active: **active (running)** since Wed 2025-07-30 13:15:51 CEST; 16h ago
Process: 1730 ExecStartPre=/opt/openziti/etc/controller/entrypoint.bash check config.yml (code=exited, status=0/SUCCESS)
Main PID: 1750 (ziti)
Tasks: 9 (limit: 2304)
Memory: 104.2M
CPU: 13min 1.672s
CGroup: /system.slice/ziti-controller.service
└─1750 /opt/openziti/bin/ziti controller run config.yml --
eric@zpix:~$
eric@ZPixR01:~$ systemctl status ziti-router.service
● ziti-router.service - OpenZiti Router
Loaded: loaded (/lib/systemd/system/ziti-router.service; **enabled**; preset: **enabled**)
Drop-In: /etc/systemd/system/ziti-router.service.d
└─override.conf
Active: **active (running)** since Wed 2025-07-30 11:43:44 CEST; 18h ago
Process: 635 ExecStartPre=/opt/openziti/etc/router/entrypoint.bash check config.yml (code=exited, status=0/SUCCESS)
Main PID: 645 (ziti)
Tasks: 7 (limit: 2304)
Memory: 102.4M
CPU: 35.202s
CGroup: /system.slice/ziti-router.service
└─645 /opt/openziti/bin/ziti router run config.yml --extend
Warning: some journal files were not opened due to insufficient permissions.
eric@ZPixR01:~$
3. https://zpix.vigitronic.eu:8440
{
"data": {
"apiVersions": {
"edge": {
"v1": {
"apiBaseUrls": [
"https://zpix.vigitronic.eu:8440/edge/client/v1"
],
"path": "/edge/client/v1"
}
},
"edge-client": {
"v1": {
"apiBaseUrls": [
"https://zpix.vigitronic.eu:8440/edge/client/v1"
],
"path": "/edge/client/v1"
}
},
"edge-management": {
"v1": {
"apiBaseUrls": [
"https://zpix.vigitronic.eu:8440/edge/management/v1"
],
"path": "/edge/management/v1"
}
},
"edge-oidc": {
"v1": {
"apiBaseUrls": [
"https://zpix.vigitronic.eu:8440"
],
"path": "/oidc"
}
},
"health-checks": {
"v1": {
"apiBaseUrls": [],
"path": "/health-checks/v1"
}
}
},
"buildDate": "2025-07-25T17:21:06Z",
"capabilities": [
"OIDC_AUTH"
],
"revision": "207d28c6bdee",
"runtimeVersion": "go1.24.1",
"version": "v1.6.6"
},
"meta": {
}
}
4. tunnel logs
(3482)[2025-07-31T03:59:14.017Z] INFO ziti-sdk:utils.c:196 ziti_log_set_level() set log level: root=4/DEBUG
(3482)[2025-07-31T03:59:14.380Z] DEBUG ziti-sdk:bind.c:108 rebind_delay_cb() server[0.28](2609) staring re-bind
(3482)[2025-07-31T03:59:14.463Z] DEBUG ziti-sdk:ziti_ctrl.c:503 ctrl_body_cb() ctrl[https://zpix.vigitronic.eu:8440] completed GET[/services/AqErEuQI8ZfkKZzPTaVvt/edge-routers] in 0.082 s
(3482)[2025-07-31T03:59:14.463Z] DEBUG ziti-sdk:bind.c:273 list_routers_cb() server[0.28](2609) zpixr01/tls://zpixr01.vigitronic.eu:8442
(3482)[2025-07-31T03:59:14.463Z] DEBUG ziti-sdk:bind.c:136 process_bindings() server[0.28](2609) checking router[zpixr01]
(3482)[2025-07-31T03:59:14.463Z] DEBUG ziti-sdk:bind.c:537 start_binding() server[0.28](2609) requesting BIND on ch[zpixr01]
(3482)[2025-07-31T03:59:14.482Z] DEBUG ziti-sdk:bind.c:514 bind_reply_cb() server[0.28](2609) failed to bind on router[zpixr01]: OK
(3482)[2025-07-31T03:59:14.482Z] DEBUG ziti-sdk:bind.c:198 schedule_rebind() server[0.28](2609) scheduling re-bind(attempt=81) in 29.954s
(3482)[2025-07-31T03:59:14.560Z] DEBUG ziti-sdk:bind.c:108 rebind_delay_cb() server[0.79](4900) staring re-bind
(3482)[2025-07-31T03:59:14.565Z] DEBUG ziti-sdk:bind.c:108 rebind_delay_cb() server[0.159](rdp) staring re-bind
(3482)[2025-07-31T03:59:14.632Z] DEBUG ziti-sdk:posture.c:213 ziti_send_posture_data() ztx[0] posture checks must_send set to TRUE, new_session_id[FALSE], must_send_every_time[TRUE], new_controller_instance[FALSE]
(3482)[2025-07-31T03:59:14.643Z] DEBUG ziti-sdk:ziti_ctrl.c:503 ctrl_body_cb() ctrl[https://zpix.vigitronic.eu:8440] completed GET[/services/6vud897IStOAIB6aa2t1rd/edge-routers] in 0.082 s
(3482)[2025-07-31T03:59:14.643Z] DEBUG ziti-sdk:bind.c:273 list_routers_cb() server[0.79](4900) zpixr01/tls://zpixr01.vigitronic.eu:8442
(3482)[2025-07-31T03:59:14.643Z] DEBUG ziti-sdk:bind.c:136 process_bindings() server[0.79](4900) checking router[zpixr01]
(3482)[2025-07-31T03:59:14.643Z] DEBUG ziti-sdk:bind.c:537 start_binding() server[0.79](4900) requesting BIND on ch[zpixr01]
(3482)[2025-07-31T03:59:14.662Z] DEBUG ziti-sdk:bind.c:514 bind_reply_cb() server[0.79](4900) failed to bind on router[zpixr01]: OK
(3482)[2025-07-31T03:59:14.662Z] DEBUG ziti-sdk:bind.c:198 schedule_rebind() server[0.79](4900) scheduling re-bind(attempt=73) in 22.695s
(3482)[2025-07-31T03:59:14.665Z] DEBUG ziti-sdk:ziti_ctrl.c:503 ctrl_body_cb() ctrl[https://zpix.vigitronic.eu:8440] completed GET[/services/1cXQqC5s6i4VFzW67tKmvo/edge-routers] in 0.099 s
(3482)[2025-07-31T03:59:14.665Z] DEBUG ziti-sdk:bind.c:273 list_routers_cb() server[0.159](rdp) zpixr01/tls://zpixr01.vigitronic.eu:8442
(3482)[2025-07-31T03:59:14.665Z] DEBUG ziti-sdk:bind.c:136 process_bindings() server[0.159](rdp) checking router[zpixr01]
(3482)[2025-07-31T03:59:14.665Z] DEBUG ziti-sdk:bind.c:537 start_binding() server[0.159](rdp) requesting BIND on ch[zpixr01]
(3482)[2025-07-31T03:59:14.684Z] DEBUG ziti-sdk:bind.c:514 bind_reply_cb() server[0.159](rdp) failed to bind on router[zpixr01]: OK
(3482)[2025-07-31T03:59:14.684Z] DEBUG ziti-sdk:bind.c:198 schedule_rebind() server[0.159](rdp) scheduling re-bind(attempt=83) in 24.383s
(3482)[2025-07-31T03:59:15.307Z] DEBUG ziti-sdk:bind.c:108 rebind_delay_cb() server[0.64](2609) staring re-bind
(3482)[2025-07-31T03:59:15.396Z] DEBUG ziti-sdk:ziti_ctrl.c:503 ctrl_body_cb() ctrl[https://zpix.vigitronic.eu:8440] completed GET[/services/AqErEuQI8ZfkKZzPTaVvt/edge-routers] in 0.089 s
(3482)[2025-07-31T03:59:15.396Z] DEBUG ziti-sdk:bind.c:273 list_routers_cb() server[0.64](2609) zpixr01/tls://zpixr01.vigitronic.eu:8442
(3482)[2025-07-31T03:59:15.396Z] DEBUG ziti-sdk:bind.c:136 process_bindings() server[0.64](2609) checking router[zpixr01]
(3482)[2025-07-31T03:59:15.396Z] DEBUG ziti-sdk:bind.c:537 start_binding() server[0.64](2609) requesting BIND on ch[zpixr01]
(3482)[2025-07-31T03:59:15.416Z] DEBUG ziti-sdk:bind.c:514 bind_reply_cb() server[0.64](2609) failed to bind on router[zpixr01]: OK
(3482)[2025-07-31T03:59:15.416Z] DEBUG ziti-sdk:bind.c:198 schedule_rebind() server[0.64](2609) scheduling re-bind(attempt=77) in 25.350s
(3482)[2025-07-31T03:59:15.803Z] DEBUG ziti-sdk:bind.c:108 rebind_delay_cb() server[0.76](2609) staring re-bind
(3482)[2025-07-31T03:59:15.887Z] DEBUG ziti-sdk:ziti_ctrl.c:503 ctrl_body_cb() ctrl[https://zpix.vigitronic.eu:8440] completed GET[/services/AqErEuQI8ZfkKZzPTaVvt/edge-routers] in 0.083 s
...
Thanks,