Hi guys,
I am new to OpenZiti and so far it looks promsing.
Controller: v1.6.7
ZAC: 3.12.5
While trying to connect to ZAC to our SSO solution (Entra), everything in the configuration looks perfect but I am unable to logs in.
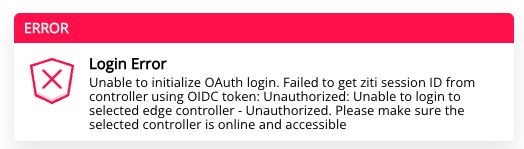
The error I recive in the UI is:
When looking on Ziti’s logs:
{"file":"github.com/openziti/ziti/controller/model/authenticator_mod_ext_jwt.go:285","func":"github.com/openziti/ziti/controller/model.(*AuthModuleExtJwt).pubKeyLookup","issuer":"https://sts.windows.net/<tenant-id-censored>/","kid":"HS23b7Do7TcaU1RoLHwpIq24VYg","knownIssuers":["https://login.microsoftonline.com/<tenant-id-censored>/v2.0","https://login.microsoftonline.com/<tenant-id-censored>/v2.0","https://login.microsoftonline.com/<tenant-id-censored>/v2.0"],"level":"error","method":"ext-jwt","msg":"issuer not found, issuers are bit-for-bit compared, they must match exactly","time":"2025-10-09T16:47:14.469Z"} {"authMethod":"ext-jwt","file":"``github.com/openziti/ziti/controller/model/authenticator_mod_ext_jwt.go:422","func":"github.com/openziti/ziti/controller/model.(*AuthModuleExtJwt).process","level":"error","msg":"encountered`` 1 candidate JWTs and all failed to validate for primary authentication, see the following log messages","time":"2025-10-09T16:47:14.469Z"} {"authMethod":"ext-jwt","error":"jwt failed to parse: token is unverifiable: error while executing keyfunc: INVALID_AUTH: The authentication request failed","expectedAudience":"","file":"github.com/openziti/ziti/controller/model/authenticator_mod_ext_jwt.go:88","func":"github.com/openziti/ziti/controller/model.(*candidateResult).LogResult","issuer":"","level":"error","msg":"failed to validate candidate JWT at index 0","time":"2025-10-09T16:47:14.469Z","tokenAudiences":""}
I looked at other posts and verified that the user must to be an admin (it is) and I also ran:
ziti ops verify ext-jwt-signer oidc --controller-url https://myctrl.mydomain.com/ Entra --authenticate
The response is looking as it should (I think ![]() ):
):
INFO using supplied redirect url: http://localhost:20314/auth/callback
INFO found external JWT signer
INFO - issuer: https://login.microsoftonline.com/<tenant-id-censored>/v2.0
INFO - clientId: <client-id-censored>
INFO supplied issuer matches discovered issuer: https://login.microsoftonline.com/<tenant-id-censored>/v2.0
Any idea what I am been missing as it does not look like something related to Auth_policy or JWT_signer configuration..
Thanks!