Hi OpenZiti Team ![]() ,
,
I’ve encountered two issues after modifying the default authentication policy on my Ziti controller using ZAC, that I would need help with. One is a minor inconsistency, and the other is more concerning from my point of view.
Incorrect JSON Key for Numeric Password Requirement
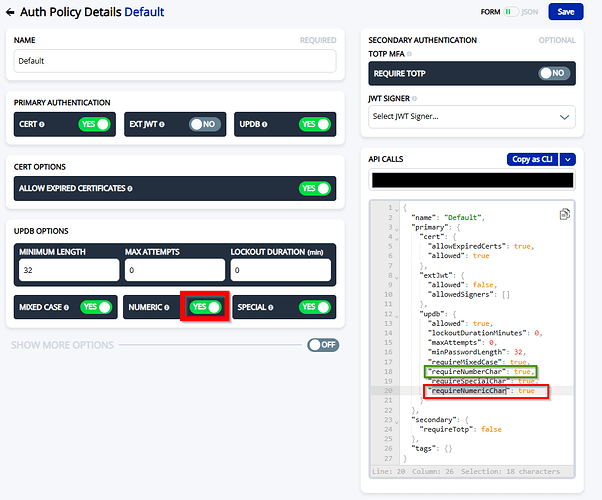
When enabling the “Numeric” password requirement via ZAC, the UI adds the key requireNumericChar to the JSON object, prepared for sending to the controller. However, based on your API documentation and my testing, the controller expects the key to be requireNumberChar.
Here’s a screenshot illustrating the issue:
Admin Login Blocked After Changing maxAttempts
After updating the maxAttempts setting in the auth policy, I’m unable to log in with the admin user—even when entering the correct password on the first attempt.
The controller logs show:
{"attempts":44,"authMethod":"password","authPolicyId":"default","authenticatorId":"XzXfdTDB3v","file":"github.com/openziti/ziti/controller/model/authenticator_mod_updb.go:127","func":"github.com/openziti/ziti/controller/model.(*AuthModuleUpdb).Process","identityId":"HwHBhpuBO","level":"error","maxAttempts":3,"msg":"updb auth failed, max attempts exceeded","time":"2025-08-13T08:48:15.930Z","username":"admin"}
This results in the Default Admin identity being temporarily disabled (for one minute, for testing). The identity object reflects this state:
{
"createdAt": "2023-06-30T12:37:39.152Z",
"id": "HwHBhpuBO",
"tags": {},
"updatedAt": "2025-08-13T08:48:15.930Z",
"appData": {},
"authPolicy": {
"_links": {
"self": {
"href": "./auth-policies/default"
}
},
"entity": "auth-policies",
"id": "default",
"name": "Default"
},
"authPolicyId": "default",
"authenticators": {
"updb": {
"id": "XzXfdTDB3v",
"username": "admin"
}
},
"defaultHostingCost": 0,
"defaultHostingPrecedence": "default",
"disabled": false,
"disabledAt": "2025-08-13T08:48:15.930Z",
"disabledUntil": "2025-08-13T08:49:15.930Z",
"edgeRouterConnectionStatus": "offline",
"enrollment": {},
"envInfo": {},
"externalId": null,
"hasApiSession": false,
"hasEdgeRouterConnection": false,
"isAdmin": true,
"isDefaultAdmin": true,
"isMfaEnabled": false,
"name": "Default Admin",
"roleAttributes": null,
"sdkInfo": {},
"serviceHostingCosts": {},
"serviceHostingPrecedences": {},
"type": {
"_links": {
"self": {
"href": "./identity-types/Default"
}
},
"entity": "identity-types",
"id": "Default",
"name": "Default"
},
"typeId": "Default",
"badges": [
{
"label": "Offline",
"class": "offline",
"circle": "false"
}
]
}
Even after re-enabling the identity via the API:
curl 'https://xxx/edge/management/v1/identities/HwHBhpuBO/enable'
-X 'POST'
-H 'accept: application/json'
-H 'content-type: application/json'
-H 'zt-session: XXXXX'
{"data":{},"meta":{}}
I still receive the following error when attempting to log in:
{"authMethod":"password","authenticatorId":"bCCsIpKVa","disabledAt":"2025-08-13T08:53:02.388984605Z","disabledUntil":"2025-08-13T08:54:02.388984605Z","file":"github.com/openziti/ziti/controller/model/authenticator_mod_updb.go:105","func":"github.com/openziti/ziti/controller/model.(*AuthModuleUpdb).Process","identityId":"cjXVI2Kja9","level":"error","msg":"authentication failed, identity is disabled","time":"2025-08-13T08:53:08.774Z","username":"tds-core-services-backend"}
The way on how to recover from this error was to use a different admin user (which I luckily had ![]() ) and set the
) and set the maxAttempts setting on the auth-policy back to 0.
And one more question, regarding the minPasswordLength, does changing that affect already set passwords, I assume not ? Does it get enforced on future password changes ?
Environment Details
- Ziti Controller Version: v1.5.4
Please let me know if there’s a workaround or if I’ve missed something in the configuration. I’d be happy to provide more details if needed.
Thanks for your support!
Best regards,
Jan